2.1.f (iv) Loopguard, Rootguard
RootGuard
Root guard makes sure that if we receive a superior BPDU on certain ports that we don’t trust them, and we can put the port into blocking state. Root guard should be enabled on “edge” or access ports. It’s usually accompanied by portfast. When a superior BPDU comes in, our ports go into root inconsistent-state. If inferior BPDUs come to that port, the port should come back up.
Another way to iterate this is root guard prevents designated ports from turning into root ports if they receive superior BPDUs.
Remember, Rootguard only protects your root bridge from changing, it doesn’t block people from adding extra switches with inferior BPDUs.
The best place to use root guard is on your Core switches facing downstream to the distribution/agg. You also would use it on your agg/dist switches facing downstream to access switches
Config – conf-if# spanning-tree guard root
Verify – “show spanning-tree inconsistentports”
Verify – “show spanning-tree”
Here’s the trigger:
![]()
Loop Guard
Loop guard protects against unidirectional link failures (BPDUs only going one way). The switching loop is prevented, and the port is basically blocked. However it alerts you that there is something wrong with the cable and you should repair it. Remember loopguard should be enabled on root and alternate ports. These are ports that lead to other switches. If a port is blocking and then it’s max age timer gets to 0 due to no BPDUs, the port is put into an inconsistent state. This is because it assumes there is probably something wrong with the switch not sending you BPDUs or that the wire is bad. Normally if the path was really loop free that switch would send BPDUs to us trying to become root, and if we all of the sudden stop getting those, we know something is wrong. Loop guard assumes that the redundant path probably did not turn to a real path. Once it starts receiving BPDUs it can recover, by either going blocking, or just receiving inferior BPDUs.
LoopGuard SHOULD be ran with UDLD (they do the same thing differently).
Loopguard is disabled by default (globally and per port)
Config-
Conf# spanning-tree loopguard default
Conf-if# spanning-tree guard loop
verification:
show spanning-tree summary
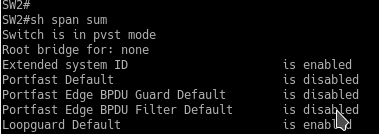
note this verification command will only tell if the default is on, if you want to check the link use
show spanning-tree int g0/1 detail
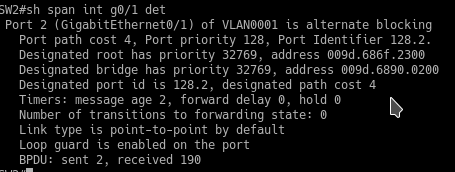
Here’s a test
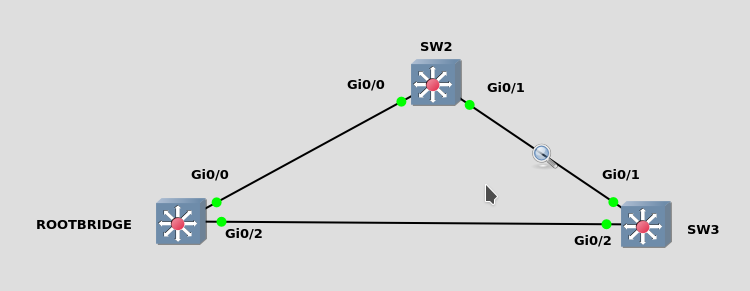
Note: SW2 G0/1 is a port role of alternative and a state of blocking. While SW3 g0/1 is a port role of designated and state of forwarding.
Let’s jump on switch 2 and enable loop guard:
SW2:
en
conf t
spanning-tree loopguard default
Now here is how we test, since G0/1 is blocking, if it stops receiving BPDUs it will let it’s max age timer hit 0, then it will try to set that port to forwarding.
We can simulate this by enabling BPDU filter on the port
conf t
int g0/1
spanning-tree bpdufilter enable
After 20 seconds I see this.
![]()
Notice the port is put into loop inconsistent mode.
![]()
If I remove bpdufilter, it should resume normal operation if it receives an inferior BPDU (which it will)
![]()
Let’s contrast this good behavior with bad behavior, not having loopguard and running into an issue where the BPDUs are not coming (either due to a unidirectional link, or the switch downstream just having software/CPU issues sending BPDUs)
conf t
no spanning-tree loopguard default
int g0/1
no spanning-tree guard loop
shut
no shut
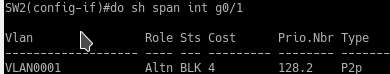
Now let’s enable BPDUfilter to simulate issues.
conf t
int g0/1
spanning-tree bpdufilter enable
AAAAAAAND THE SWITCH FROZE UP DUE TO A SPANNING-TREE LOOP.