Table of Contents
2.1.f (iii) Portfast, BPDUguard, BPDUfilter
PortFast
With RSTP this is now an open standard and is called an EDGE port, however the configuration is still very similar to 802.1d portfast
Allows a port running STP to go from blocking to forwarding immediately. This skips listening and learning (15 + 15 sec)
Should only be enabled on access switches, edge ports. Requires extra parameters to be configured
On a trunk port. Can still prevent loops.
This also prevents topology change notifications from being sent when a port goes up or down.
config:
Conf-if# spanning-tree portfast
Conf# spanning-tree portfast default
conf# spanning-tree portfast bpdufilter default
conf# spanning-tree portfast bpduguard default
The commands enable port fast by default, any non hosts or edge ports should have “no spanning-tree portfast” configured.
Note that this only enables it on ports that you are NOT receiving BPDUs on.
if the link is a trunk it will not affect it, you must use the following command (mostly for servers)
conf t
int g0/1
spanning-tree portfast trunk
Verify
Show spanning-tree interface <int> portfast
The above will tell you if portfast is enabled on a port and what vlan.
Here is an example.
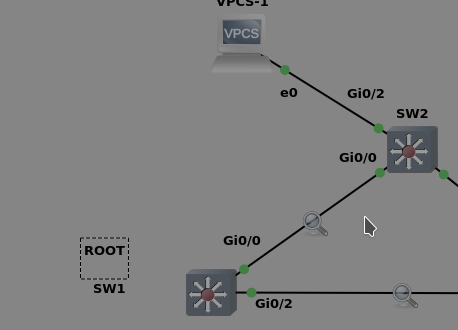
We are on SW2 and we bring up the link of g0/2 to a host, that IS configured for portfast.
This is the only BPDU that came on the link between SW(root) and SW2(non-root).
We get what we expected, only BPDUs from root (SW2 will never send BPDU on it’s root port)
That’s what port-fast does, it prevents TCN BPDUs from being sent out.
Now here is the same example, but let’s run the command to remove portfast “no spanning-tree portfast” on that int g0/2
Now here is the capture from the link between SW1 and SW2. SW2 who normally never sends BPDUs out of it’s root port now sends a TCN BPDU via it’s root port.
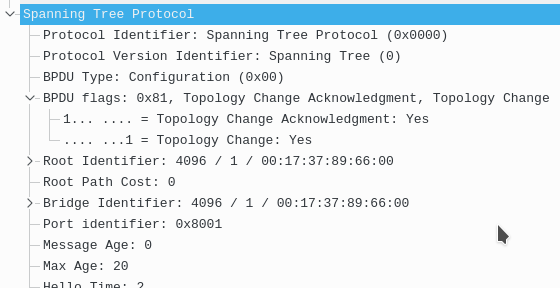
Now here is SW1(root) sending the TCA BPDU back to SW2 acknowledging the message.
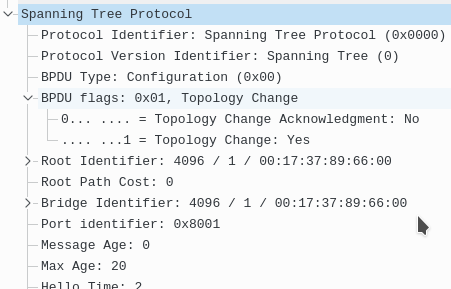
Now SW1(root) sends this BPDU out to ALL switches in the tree stating they need to set their CAM table timeout to max age, in this case 20 sec (default)
UplinkFast
A legacy feature to STP, now with RSTP this is implemented in the protocol.
With 802.1D if our root port dies and we have a backup link, that alternative/backup link will take 15 sec of listening and 15 sec of learning before it can go up. This wastes time.
UplinkFast changes that.
If our root port dies, our backup port/Alternate will immediately go to forwarding. Cisco recommends only using this for your access switches. It should only be used on dist and access layer switches. NEVER ON THE CORE. And if you enable it, it increases your switch’s STP priority to make sure it will never be root. Uplinkfast can only be enabled per switch, not per port, and not per vlan. The original root port can become the root port again, it can preempt that role. The switch will wait 2 x forward delay + 5 seconds before the primary root port enters forwarding.
config:
Conf# spanning-tree uplinkfast
verification : show spanning-tree summary
verification: show spanning-tree uplinkfast
When we run “show spanning-tree” our local switches priority will go up, and our root port costs go up. 3k is added to the link costs. If our switch was the root bridge, it will no longer be. You will also see “uplink fast enabled” on the output of the previous command. The switch priority goes up to 49,152 + vlan ID. This is how cisco makes sure you don’t run this on dist or core switches. Our cutover to the new root port works great however other switches need to update their CAM table for new entries. These take a few seconds to update but we can make it even faster. What happens is our switch that got a new root port will now send “dummy” multicast frames to its new root port (other switch) with dst of 0100.0ccd.cdcd and the source mac of every entry in the cam table. This effectively, and quickly updates that CAM table of the switch that took over. The default of how often those are sent is 150pps. You shouldn’t have to mess with this.
Conf# spanning-tree uplinkfast max-update-rate <max number of dummy multicast to send per second>
The above is used if you have a huge CAM table in your local switch. You can disable sending the dummy frames by sending it to 0. Again, not recommended to change this to anything lower.
Example:
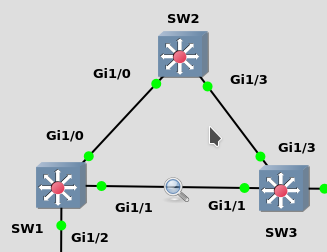
SW1-3 are running PVST (NOT RAPID PVST)
SW3 is the root.
Currently on SW3 the root port is of course G1/3, it has the lowest cost to root (4).
So obviously just by looking at the diagram the link between SW1 and SW2 is going to be blocked.
SW2’s alternate port will need to go from the state of blocking to listening to learning and then finally to forwarding. When I tested it, it took 30 seconds.
We know that uplink fast should be enabled all all switches EXCEPT for the root bridge and secondary bridge.
Let’s do that.
SW1 and SW2:
en
conf t
spanning-tree uplinkfast
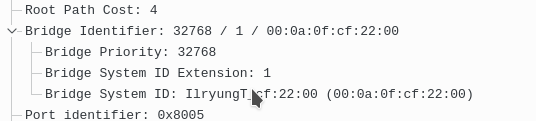
Here’s their BPDU changes
before:
After:
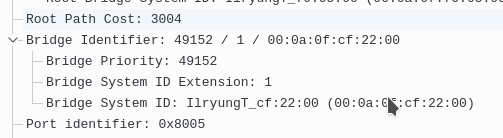
Like we stated earlier 3k is added to root path cost and the bridge priority went up to 49152.
Now let’s simulate the failure on SW2’s root port.
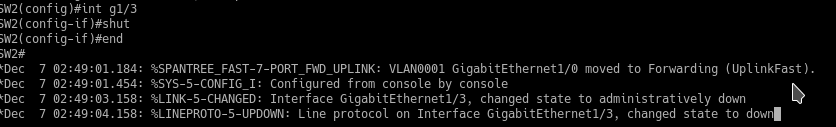
Boom immediate forwarding.
This might sound great to you. However realize that this doesn’t ALWAYS work. For this to work you MUST have a alternate port.
If your switch is the side of the blocked link that is designated forwarding, this will NOT work.
For example let’s undo everything, return the root port to be g1/3 and then we will hop over to SW1 and shut off his root port.
SW1:
en
conf t
int g1/1
shut
Now his other port that was designated forwarding becomes a root port
![]()
You might wonder, ok great what’s the problem with that? Well the other side (SW2) shows this.
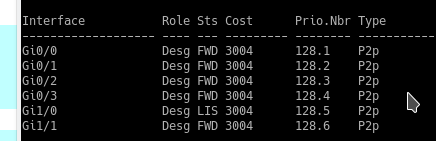
In this scenario since SW1 has NO alternate ports, it CANNOT utilize uplink fast.
BackboneFast
A legacy feature to STP, now with RSTP this is implemented in the protocol.
Helps our network to recover from in-direct link failures. A failure of a link not directly connected to our switch. This happens when an inferrio BPDU is received.
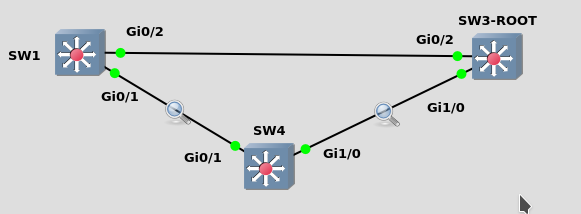
SW1’s root port is g0/2
SW1’s g0/1 is a designated port
SW4’s g0/1 is a blocking port
SW4’s root port is g0/2
Backbone fast protects us from in-drect link failures. It only works if we lose our root port and the other port we have is designated!
If the other port we had was a blocked port, backbonefast is NOT what is needed as the port would go from blocking to listening.
If we wanted to speed that process up we would utilize uplinkfast.
Thus at the access layer, one should use BOTH uplinkfast and backbone fast as they serve different purposes.
In the core one can only utilize backbonefast and NOT uplinkfast.
Here is the scenario that backbonefast fixes:
if the link between SW1 and SW3 dies, SW1 will try to declare to SW4 he is root (since his port is designated).
G0/1 on SW4 is blocking so he waits until MAX AGE (20 sec by default) to answer SW1s BPDUs and tell SW1 about SW3.
That means that to recover, G0/1 on switch 4 needs to wait MAX AGE + Listening + learning.
Now with backbone fast:
If that link dies SW1 will send his BPDUs on that designated port to SW4, although that port is blocking for SW4, he sends a root link query to SW3 via his root port.
If SW3 replies then he knows SW1 lost his root port and he skips max age and goes directly into LISTENING. This shaves off 20 seconds from SW1’s recovery.
Note that Backbonefast root link queries and replies CANNOT be seen in Wireshark, you must observe them via the verify command.
Backbone needs to be enabled on ALL switches on the network.
Config – Conf# spanning-tree backbonefast
Verify: Show spanning-tree backbonefast
Here is an example of triggering it:
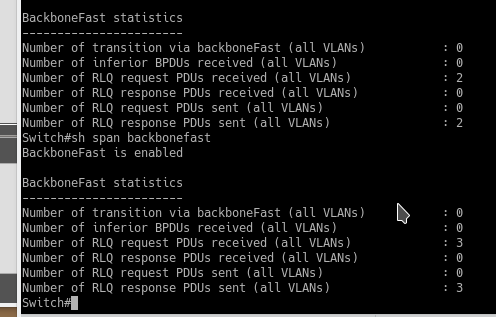
>BPDU Filter
BPDU Filter prevents ANY BPDUs from leaving or being received on portfast enabled ports. Can be enabled globally, or per port.
Config –
Conf# spanning-tree portfast edge bpdufilter default
Conf-if# spanning-tree bpdufilter enable
BPDUguard
BPDU guard disables a port if it receives any BPDUs on that port. The port goes into error-disabled regardless if the BPDU was superior or inferior. This does a little more than root guard. Note that the switch connected must be running some type of spanning-tree flavor for this to work. If the switch doesn’t accept BPDUs or doesn’t run spanning-tree this won’t be able to detect that. With error-disabled, by default we will have to manually fix the issue by removing the extra switch and bouncing the port. BPDU guard is the more common used tool along with portfast, better than rootguard. When enabling port fast you can also enable BPDU guard. “spanning-tree portfast edge bpduguard default”.
Config – spanning-tree portfast edge bpduguard default
conf-if# spanning-tree bpduguard enable
Here’s the trigger:
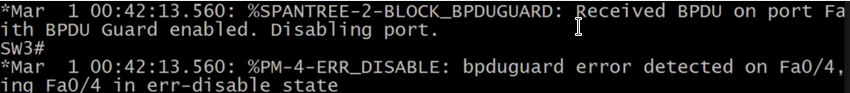
Notice that BPDU guard saw a BPDU from a different switch coming from this port, then the port is put into error disabled.
To have BPDU guard recover we will use this
Conf #
Errdisable recovery cause bpdu-guard
Errdisable recovery interval <sec>