I have a project to implement SSO for hosted JAMF/Casper Suite. First I setup the OneLogin virtual LDAP connection to JAMF. Then I found out there’s no way to mass import users. This was important to me because I wanted users to be able to self enroll with AD credentials. I didn’t want to import every single user individually. The answer? Claims based authentication.
Here’s the JAMF article I used to get the basic SSO setup
https://www.jamf.com/jamf-nation/articles/438/configuring-single-sign-on-with-onelogin
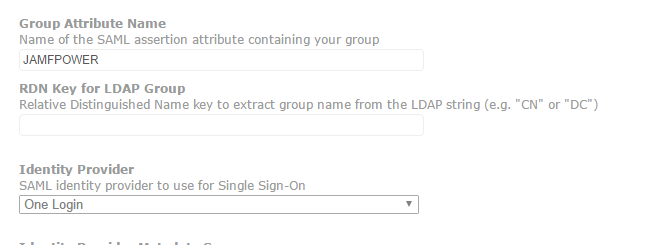
With this setup the token passed to JAMF includes the username or email and the group membership. With the setup you need to make sure you set the relative distinguished name to “CN”. That field is this.
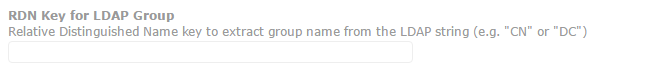
In there make sure to type “CN”.
With the above article complete, you now need to create a STANDARD JAMF/JSS group. I repeat, a standard group.
Just go to the admin panel, click user accounts
click the “+”

Create a standard group
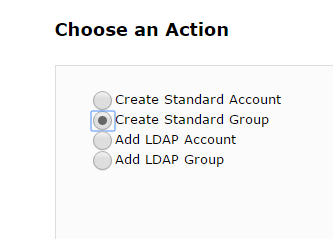
In this example I will call mine “Domain Admins”
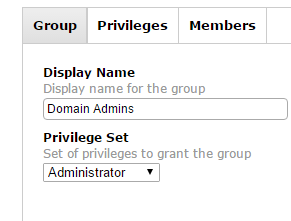
Now the group membership should be passed along, it will match this group. Thus any user that is part of the “Domain Admins” will now be logged in as an administrator into JSS/JAMF.
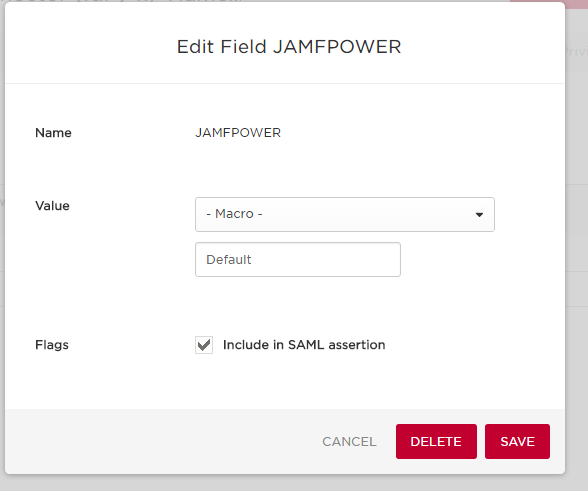
I quickly found out with this though that my goal of having every AD user enroll their own device into JAMF had one small problem. With the specific article I was passing the user’s group mebmership under the SAML assertion. The issue with that is I needed a matching group on the JAMF side. For some reason I could not pass “Domain Users”. I changed things up a little bit and just setup a static value to be passed and verified. With this every domain user can enroll into JAMF, however administrators will need to manually log in.
Here are my JSS settings
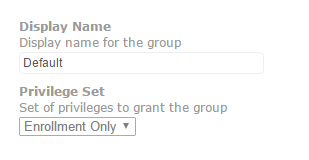
Then I created a standard group called “Default” with only the enrollment security settings
Finally here are my Onelogin Parameters that I passed, notice the static value
With the above complete my current and new domain users are able to enroll their devices into JSS/JAMF/Casper Suites.