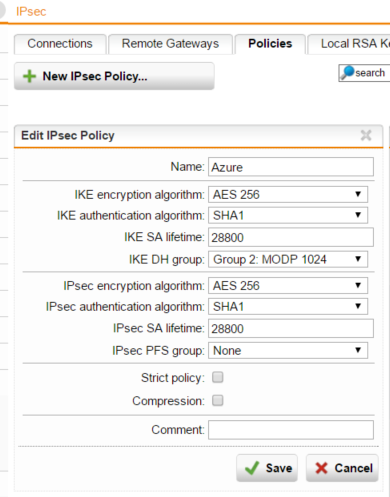
The Sophos UTM Azure Policy:
The sophos UTM Azure Remote Gateway:
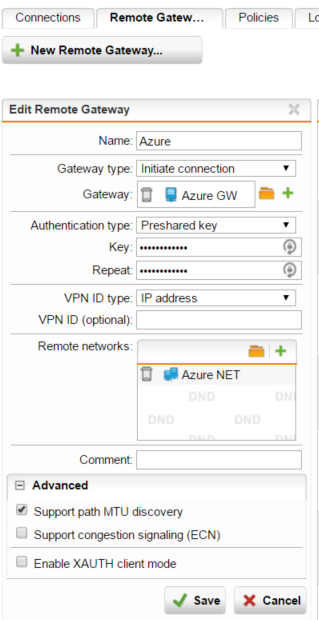
notes: the pre-shared key should match on both sides, the gateway object should be the public IP assigned to your gateway.
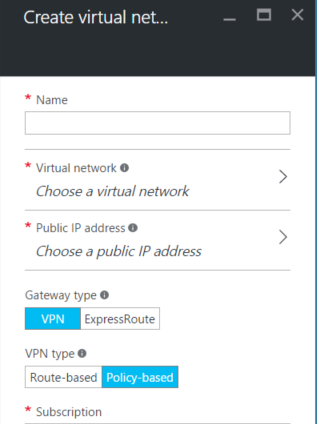
When creating your Azure Virtual network gateway, you must choose policy-based VPN, NOT route-based. Policy based is IKEv1, while route based is IKEv2. The sophos UTM only supports IKEv1. It’s also important to note Azure virtual network gateways configured this way only allow ONE SITE TO SITE VPN connection since it’s policy/ikev1. This means that if you require more VPNs to azure you can use the Sophos UTM as a VPN concentrator device and advertise the azure network over that. See below how to select policy based VPN:
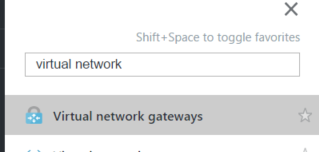
How to find your Azure virtual network gateway public IP:
Login to the azure portal, then search for virtual network gateway
Then your public IP should be on the right most setting.
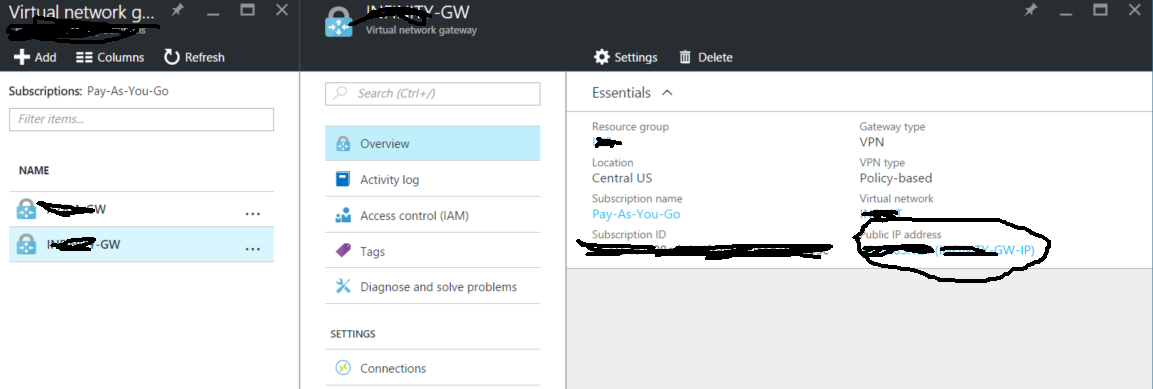
You should also verify your gateway has a static public IP and not a dynamic one or else it can change! You either need to take down the vpn or recreate the gateway for this (or just create a new public IP resource)