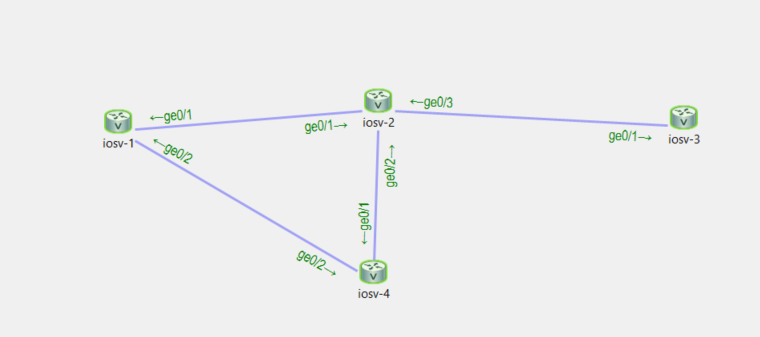
Link between R1-2 is 10.0.0.0/30
link between R1-4 is 10.0.1.0/30
Link between R2-4 is 10.0.2.0/30
Link between R2-3 is 10.0.3.0/30
R1 has a loopback of 1.1.1.1/32
R3 has a loopback of 3.3.3.3/32
We want our traffic to go from router 3 (far right) to router 4, then to router 1. We need to apply this PBR at router 2 since that is where the traffic will ingress.
First configure an access list to catch the traffic you want to apply the PBR to
iosv2# access-list 101 permit ip host 3.3.3.3 host 1.1.1.1
This will match any IP packets from 3.3.3.3/32 to 1.1.1.1/32
The implicit deny will match all other and those will be routed normally.
Now we need to create a route map
iosv2# route-map PBR permit match ip address 101 set ip next-hop 10.0.2.2
What we just did:
First we create a routemap with the name PBR,
Then we tell it to apply this PBR to the IP Packets matched in access-list 101
Then we tell it which next-hop the matched IP packets will take.
int g0/3 ip policy route-map PBR
Now we apply the PBR to the ingress interface. ( where the traffic first comes into this router from)
Now by running debug ip policy on router 2 I can verify if packets are being PBR’d
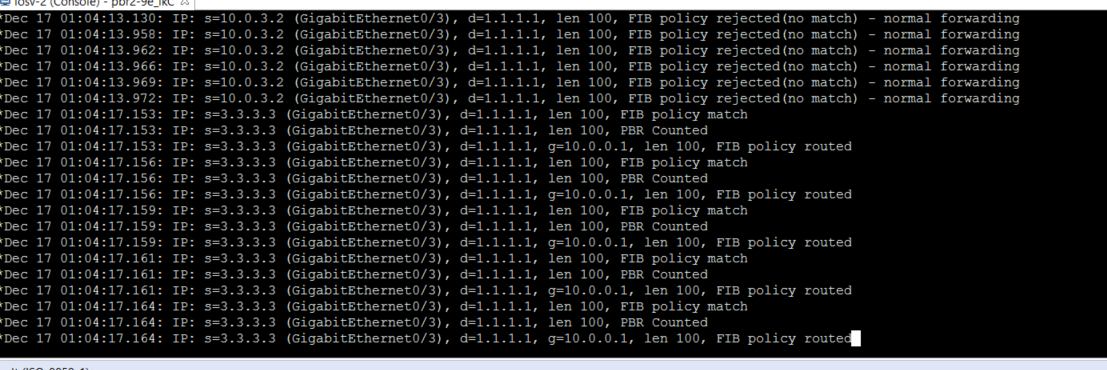

The first ping was from the closest interface (10.0.3.2) not the loopback (3.3.3.3). It didn’t match our ACL (101) so it was routed normally.
When I did a second ping from the source of 3.3.3.3 with a dest of 1.1.11. it was successful in routing it with the PBR.
The most important thing to be aware of is that PBR can notice if a line interface is down, you do NOT need to track that with IP SLA and tracking. If I have a PBR that routes traffic to g0/1 and g0/1 goes down, PBR will pass the traffic back to be normally routed. This means if I had another path, I would be able to automatically use it with a dynamic routing protocol.