This is going to be a quick config on how to configure your Cisco, HP, and Dell switches to authentication to AD via a Windows NPS Server. I am providing the config and policies that have worked for me. I even included a policy and config for the Cisco ASA.
First of all we need to add your network devices/radius clients. I prefix their names in the NPS server with their device type, this is important because my policies match on the client friendly name. I needed this because 2 types of devices (Cisco ASA and HP 1910/1920) did not play well with my default network policy. So for example here is what my ASAs and HP 1910 and 20s look like.
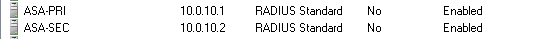
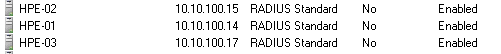
For all my other devices I named them by their regular hostname because I wasn’t matching their client friendly name. They all match the default policy I have (dell, cisco, and newer HP switches).
So here are the policies.
First of all leave the default connection request policy, basically it should always allow. Our filtering will be done in the authorization policy.
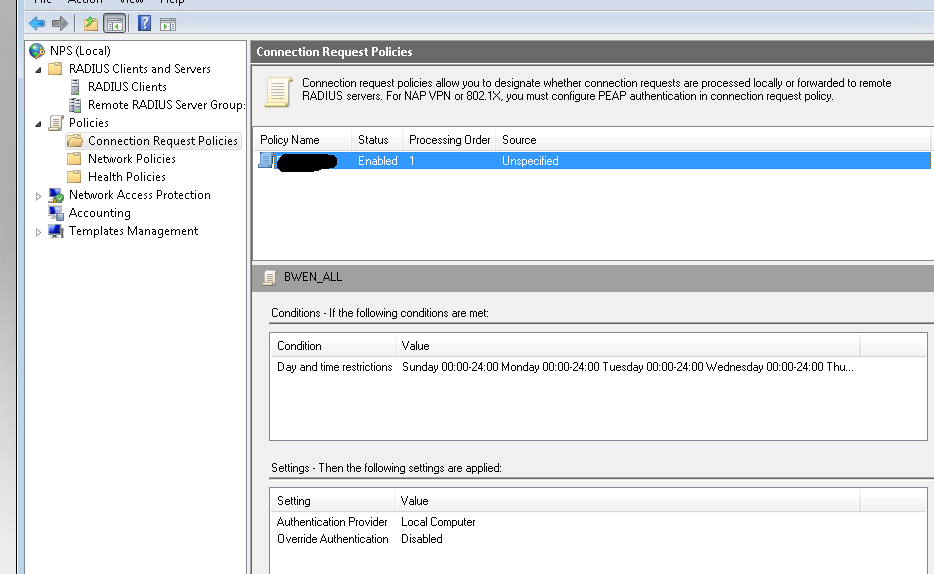
Then I have 3 new policies I created above the defaults. One for ASAs, one for the HP 1910/20s and one for everything else (Dell, newer HP, Cisco switches).
Here is the ASA policy:
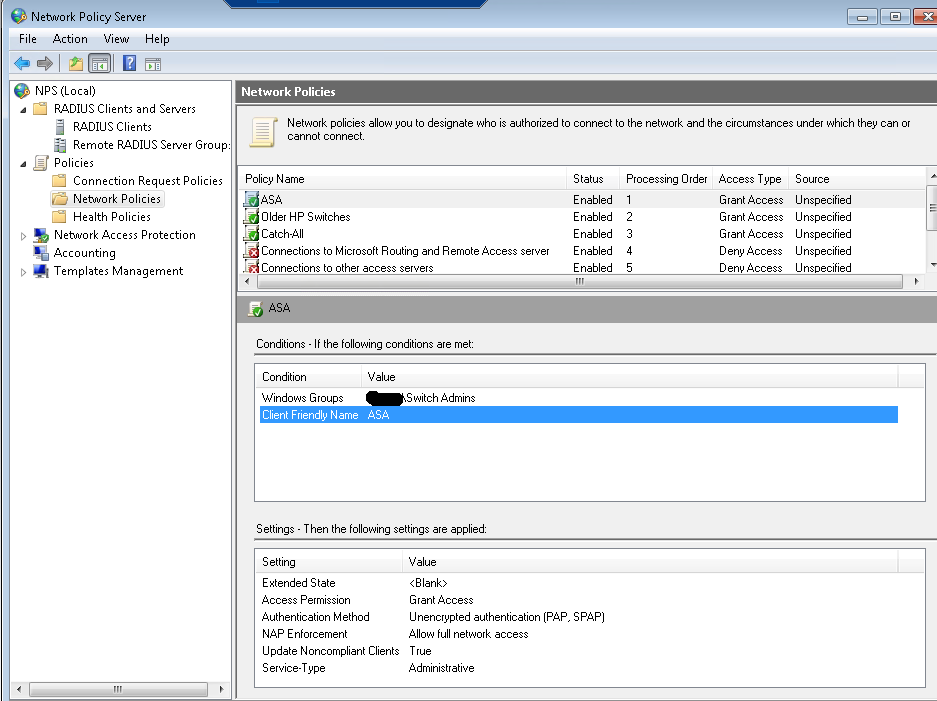
Here’s the ASA config:
aaa-server NPS protocol radius
aaa-server NPS (Inside) host x.x.x.x
key passwordhere
exit
aaa authentication http console NPS LOCAL
aaa authentication ssh console NPS LOCAL
aaa authentication telnet console NPS LOCAL
aaa authentication enable console NPS LOCAL
aaa authorization exec authentication-server auto-enable
Here’s the policy for HP 1910’s and 20 style switches:
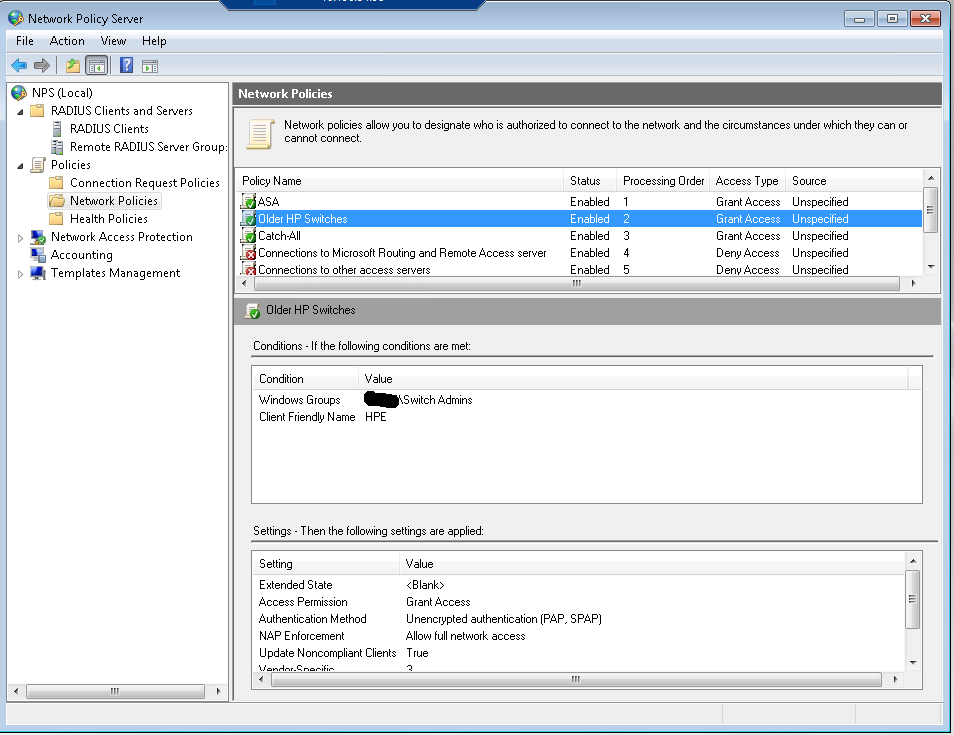
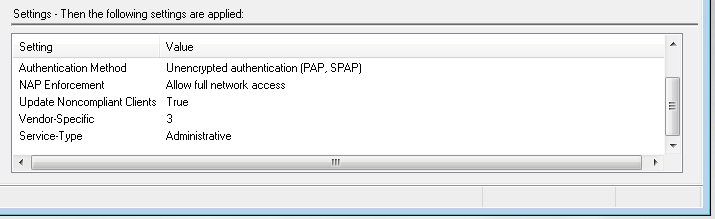
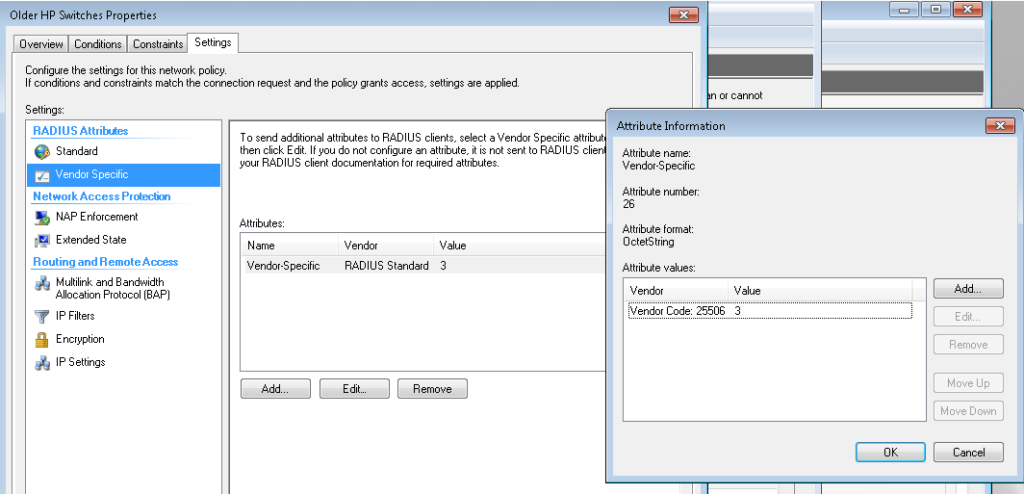
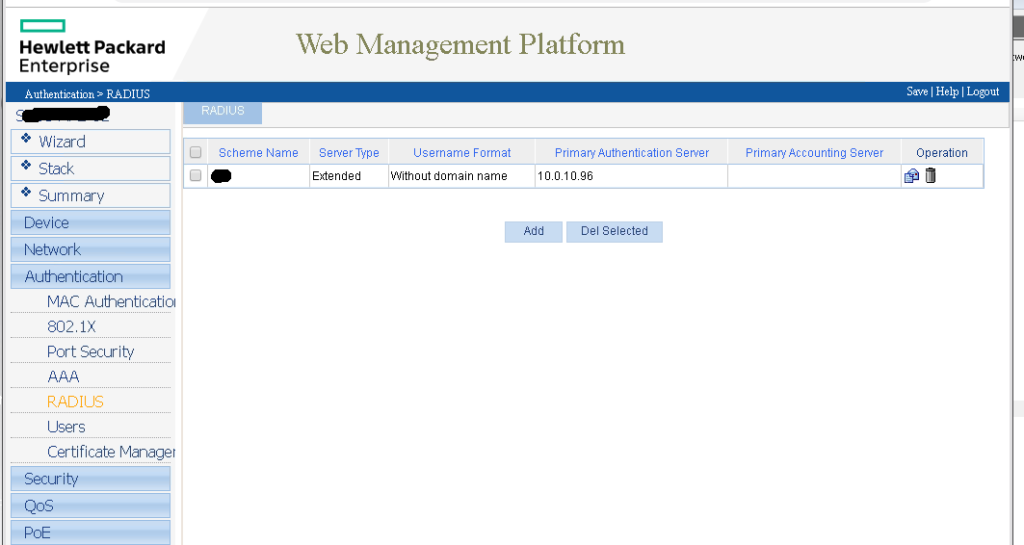
Here is the GUI config from an HP 1920, there’s a lot of screenshots so be prepared
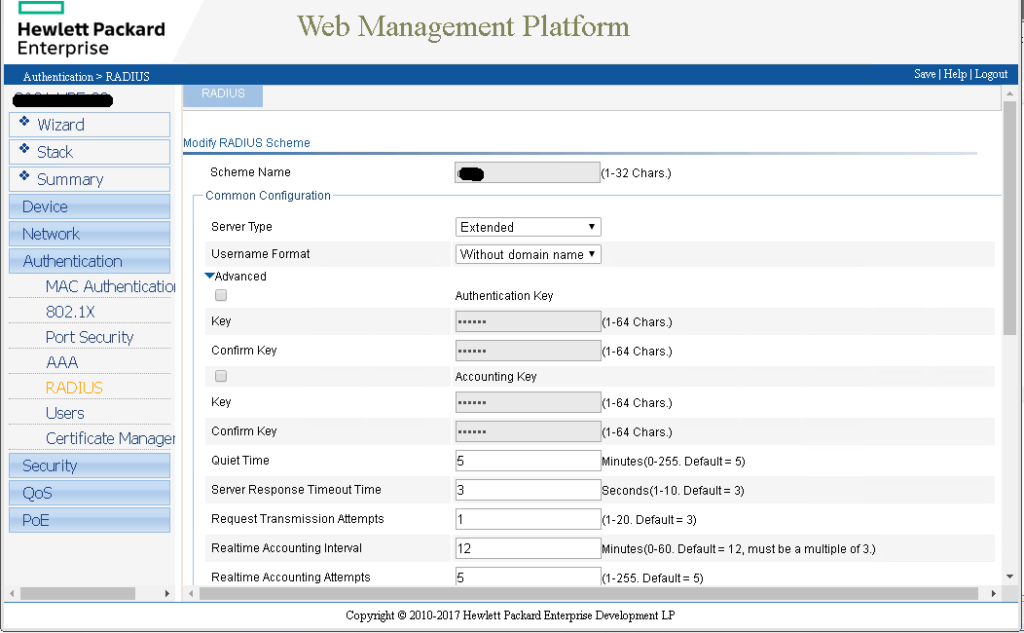
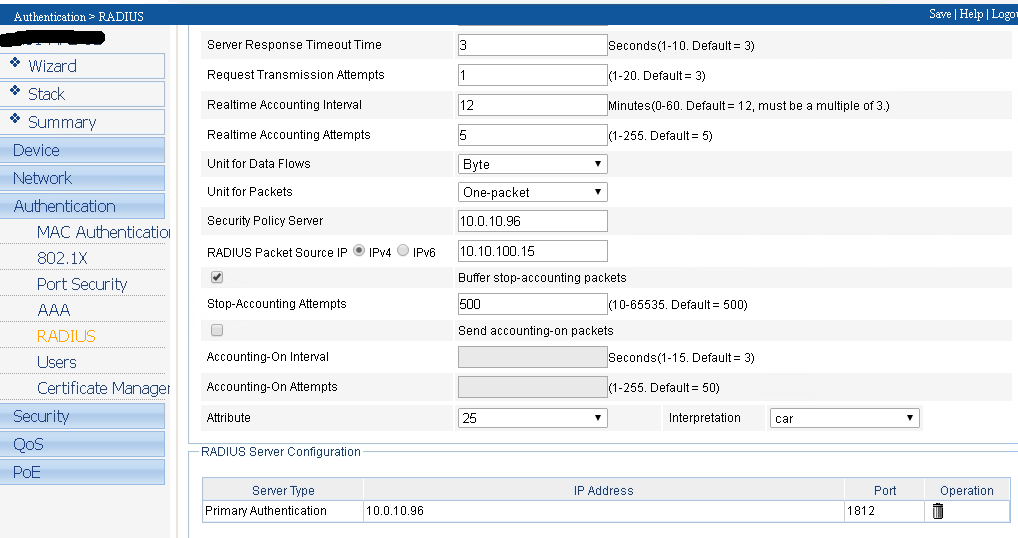
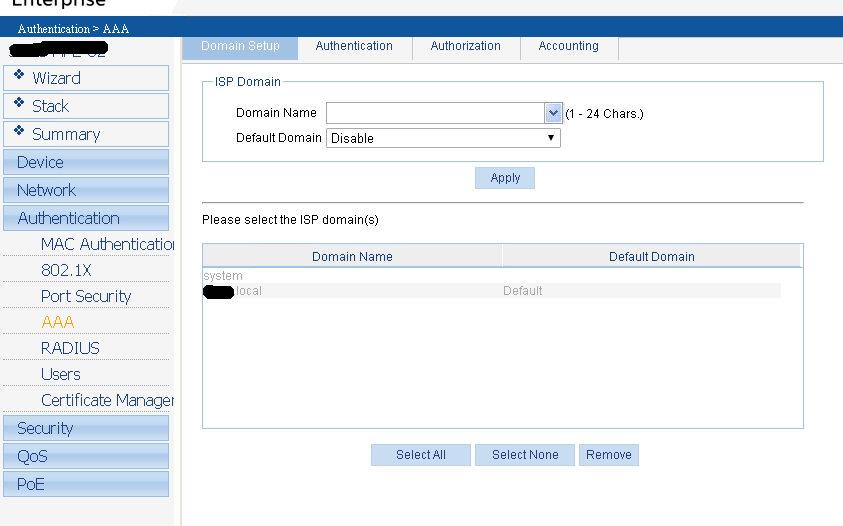
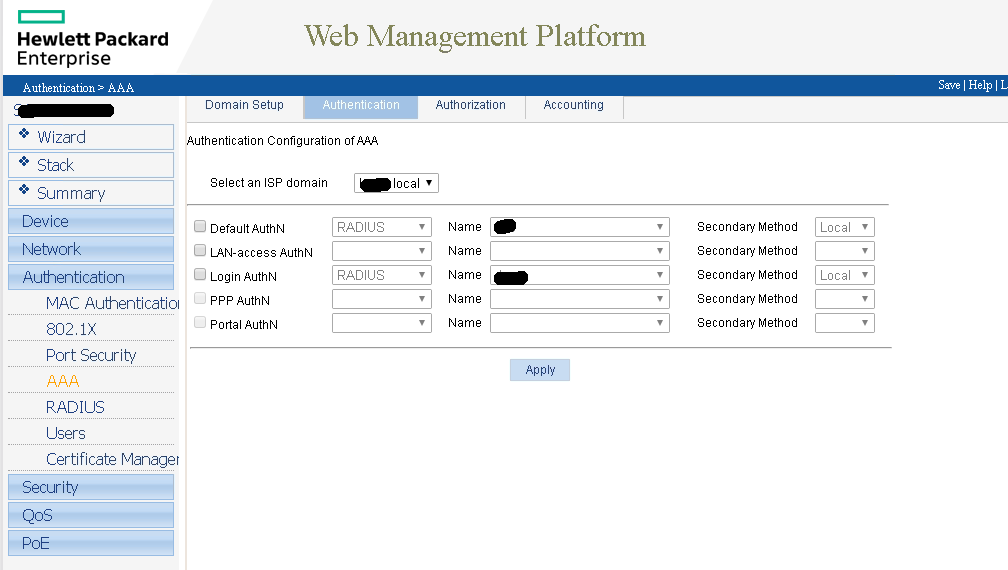
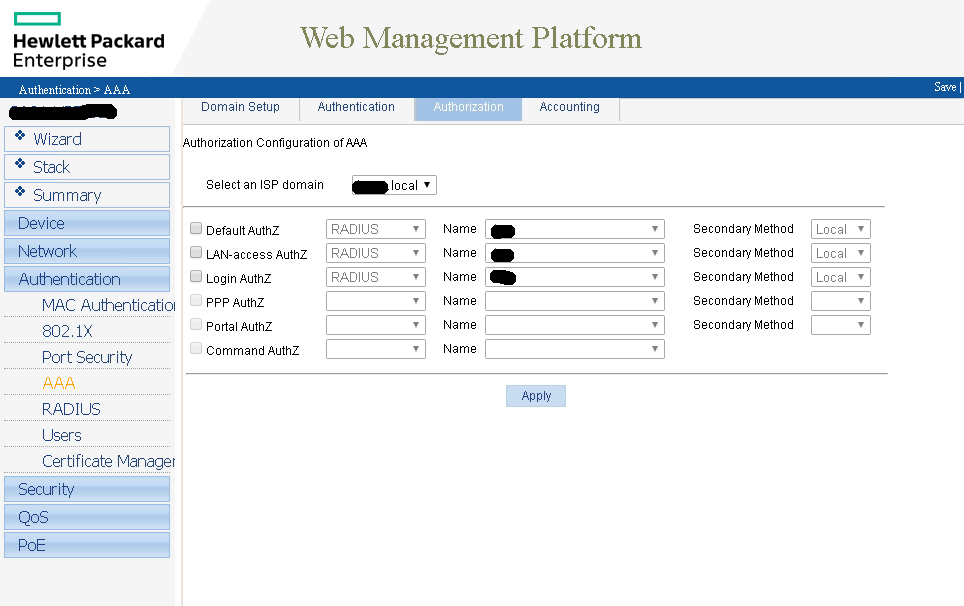
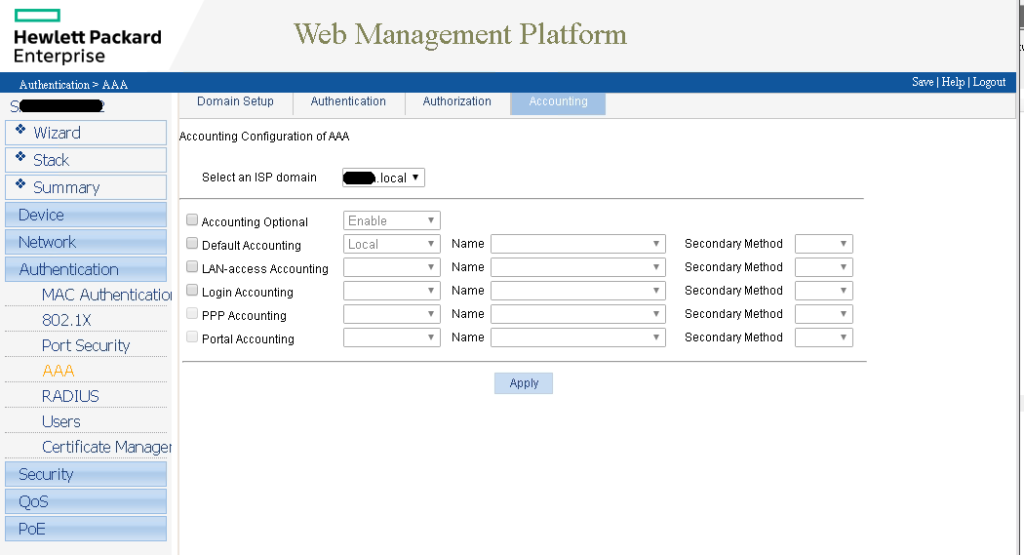
And now for the catch all policy I use for all other Cisco, HP, and Dell devices.
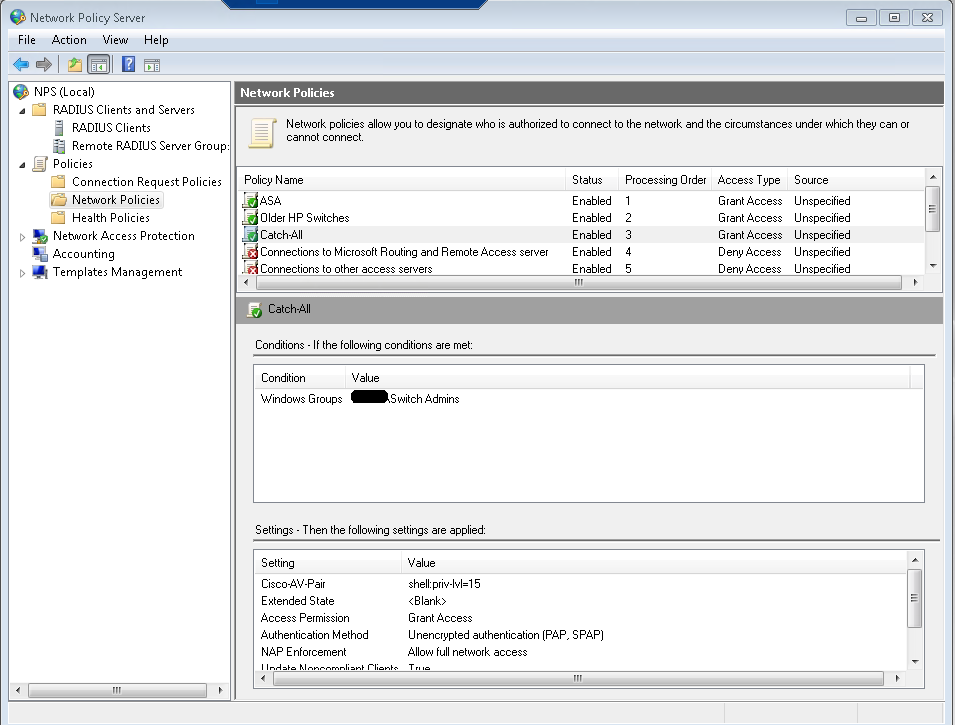
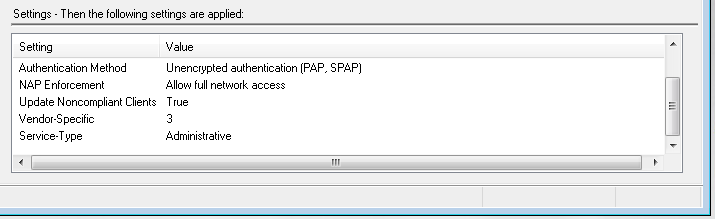
Here is config from a Dell Power connect 6248P. Note that the enable password is empty. There’s no easy way around this due to some software issue. In newer code I believe it’s fixed.
configure
radius-server host auth x.x.x.x
name “NPS”
timeout 10
retransmit 10
key “XXXXXX”
exit
no enable password
!This is required on old code as it can’t do authorization exec
aaa authentication login “NPS” radius local
aaa authentication enable “NPS” enable
ip http authentication radius local
ip https authentication radius local
line telnet
login authentication NPS
enable authentication NPS
exit
line ssh
login authentication NPS
enable authentication NPS
exit
ip ssh server
Finally here’s a working config for Cisco Routers and switches.
aaa new-model
ip radius source-int X
radius server NPS
address ipv4 x.x.x.x auth-port 1812 acct-port 1813
timeout 10
retransmit 10
key XXXXXXX
exit
aaa authentication login default group radius local
aaa authorization exec default group radius local