IPv4 Options:
Within the ipv4 options field there are actually 3 fields: Copy, Option class, and number.
The copy section tells us what the packet is for:
Datagram and control information
Debugging and management information
And a reserved field
The option class what to do with fragments:
Copy the option only into the first fragment
Copy the option into all fragments
Finally we have the Numbers field, which tells us the actual options:
End of Operation
No operating
Both of these options are using as padding the options to make them fit in the header
Loose source routing
Used to tell the routers about some routers this packet should traverse but does not have to.
Timestamp
This command causes routers to record a timestamp of when the packet arrived in the header and send it back to us.
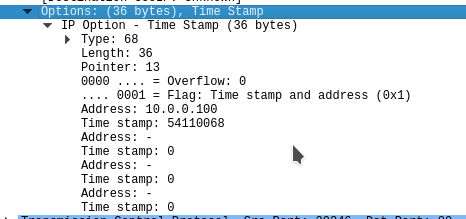
The command I used for that is
nmap -n -sP –packet-trace –ip-options “U” 10.0.0.252
Record Route
This options records all the paths that the packet took to get to the destination. These seem to be recorded/written by the routers on the path, here’s an example.
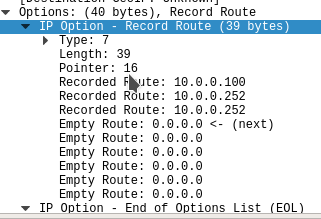
The command I used for this one was
nmap -n -sP –packet-trace –ip-options “R” 10.0.0.252
Strict Source Routing
Similar to loose source routing however this is an absolute list of the path the packet should take (security risk)
Router alert
Used for specify the IP address of a router that this packet traverses, such that the router can act upon it if configured to do so.
Security
This option is for defining a security class, it was meant for the military to tag their super top secret packets with this option. I’ve never actually seen this used in a military application yet.
Stream ID
These are obsolete
Again when using IP options the header increases from the default of 20 Bytes to something larger, it can be up to 40 bytes.
If you install nmap, it should come with nping, which can ping with IP options so you can verify these details.
Here’s an example I found
sudo nping -icmp -c 1 -icmp-type 8 –ip-options “\x94\x04\x00\x00” –dest-ip x.x.x.x.
source:
https://askubuntu.com/questions/448708/nmap-icmp-request-with-ip-options
https://nmap.org/book/nping-man-ip-options.html
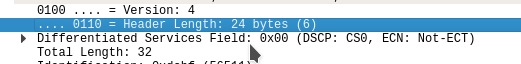
Here’s a test I did with some IP options, notice now the internet header length is 24 bytes, which is 4 more than normal.
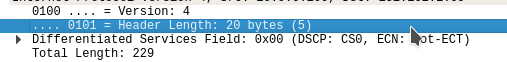
Here’s a normal IP packet with no options, with a header of 20 bytes.
IPv6 Extension headers:
Recall that in section 1.1.d Explain IP Operations, we heavily looked into the IPv6 header. In there we saw a next header field.
This field is used to either tell us about the next upper layer protocol (common) or to tell us the next IPv6 extension header.
At the end of all of the extension header packets, we will have an IP packet denoting the next header as being an upper layer protocol.
Here are the IPv6 extension header options (table taken from cisco.com):
| Order | Header | Next Header Code |
|---|---|---|
| Order | Header Type | Next Header Code |
| 1 | Basic IPv6 Header | – |
| 2 | Hop-by-Hop Options | 0 |
| 3 | Destination Options (with Routing Options) | 60 |
| 4 | Routing Header | 43 |
| 5 | Fragment Header | 44 |
| 6 | Authentication Header | 51 |
| 7 | Encapsulation Security Payload Header | 50 |
| 8 | Destination Options | 60 |
| 9 | Mobility Header | 135 |
| No next header | 59 | |
| Upper Layer | TCP | 6 |
| Upper Layer | UDP | 17 |
| Upper Layer | ICMPv6 | 58 |
The headers you are most likely to see are described below:
Hop by Hop: Used for Ipv6 Multicast Listener Discover (MLD).
Destination: Is used to denote other destinations Cisco claims this is for “IPv6 Mobility”.
Routing: Similar to source routing.
Fragmentation: Denoting IPv6 fragments done by the source host.
Mobility: Extra features for IPv6 on mobile carriers
Authentication: Similar to the auth header in IPSEC
ESP: Similar to the IPv4 ESP header and functions.
Routers that see IPv6 packets with extension headers are only required to process the Hop by Hop header and the others are optional or intended for the source or destination.
note that the hop by hop extension header cannot be CEF processed and must be sent to the punt adjacency.
IP Header sources:
http://www.networksorcery.com/enp/protocol/ip.htm#Options
http://euclid.nmu.edu/~randy/Classes/CS442/Notes/IPv6_Header.html
http://www.cc.ntut.edu.tw/~kwke/DC2006/ipo.pdf
https://www.cisco.com/en/US/technologies/tk648/tk872/technologies_white_paper0900aecd8054d37d.html
Also, wireshark is your friend here, capture and review.