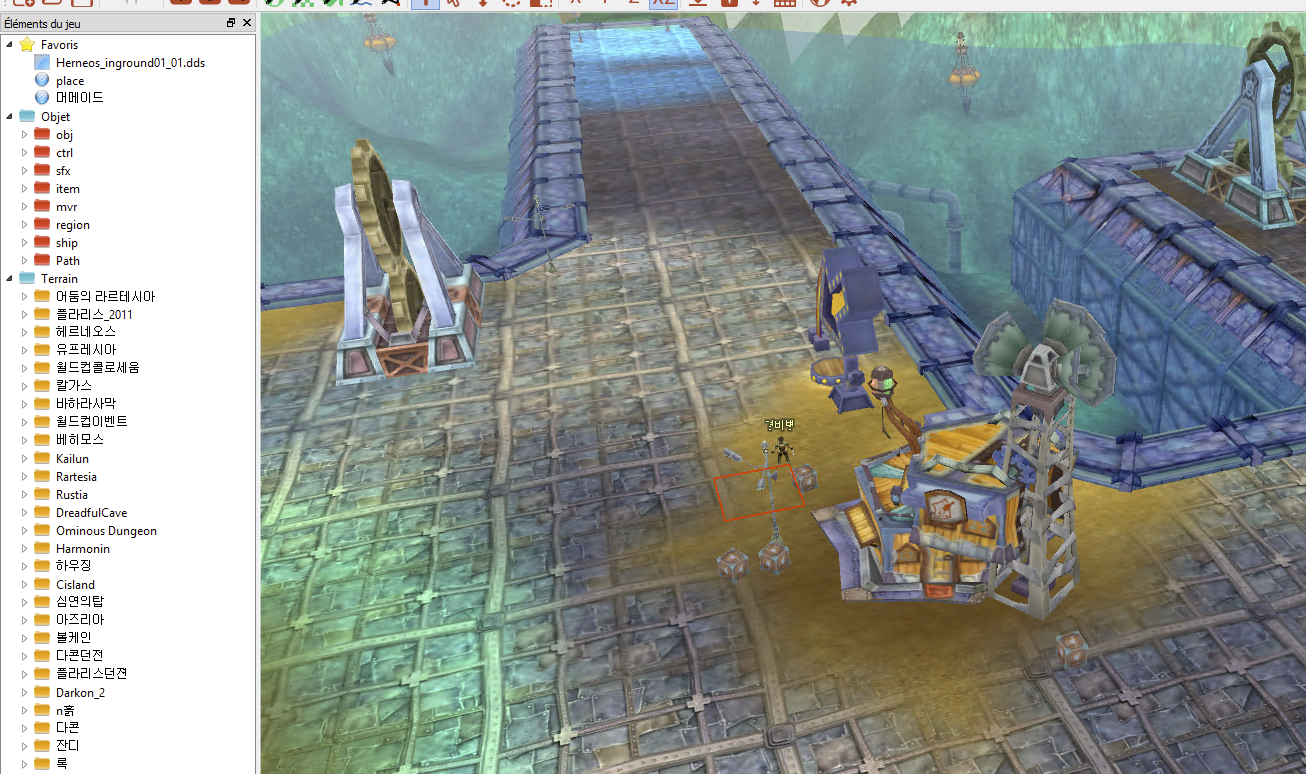
The easiest way I found to cheat in Heroes of Hammerwatch 2 is to modify the assets.bin file. However, doing this causes the game's anti-cheat to trigger and close the game with a warning. Below I show you how to defeat the anti-cheat. Here's a high-level plan: Modify the assets.bin file to change merchant behavior …
Reversing and patching Megaman Battle Network 6 in assembly – GBA ROM
Megaman Battle Network 6 - Cyberbeast Gregar takes me back to my childhood. It's a shame they discontinued the series. For some reason, none of the cheat tables for emulators worked on the money/zenny in this game. Basic memory editing of zenny always seemed to set it to 0. In my frustration, I reverse engineered …
Continue reading "Reversing and patching Megaman Battle Network 6 in assembly – GBA ROM"
Flyff ATools – compiled and ready for use
Atools is a set of custom programs created to modify and customize Flyff resource files. The files can then be used on private game servers. There are four tools included which allow you to modify everything about the game like the GUI, models of monsters and items, character models, and even the world maps. I …
Continue reading "Flyff ATools – compiled and ready for use"
How To Change Cisco FMC IP Address From CLI
So you've found yourself in a situation where you need to change the Firepower Management Center (FMC) IP address from the CLI. This guide will quickly detail how to accomplish that. Here's how to do it. Step By Step Process To Change the IP Address Of Your FMC Step 1: Log into The FMC CLI …
Continue reading "How To Change Cisco FMC IP Address From CLI"
Seagate Hard Drive Reviews: BarraCuda and IronWolf
Today, we’re going over the latest Seagate hard drive lineup of 2021: BarraCuda and IronWolf. We'll review what's good and bad about these hard drives. If you’re considering upgrading your current desktop computer’s storage, or maybe you’re looking to build a new desktop, then you’ve probably found yourself searching for information about new drives to …
Continue reading "Seagate Hard Drive Reviews: BarraCuda and IronWolf"
3 Best Nintendo Switch Keyboards You Wish You Had
We've found the 3 best Nintendo Switch keyboards. Are you looking to combine the practical aspect of a physical keyboard with the gaming experience of using a Nintendo Switch? Trying to find a way to make game chatting and typing passwords quicker and less painful? Luckily for all, there is a gadget category that makes …
Continue reading "3 Best Nintendo Switch Keyboards You Wish You Had"