The guide below will explain how to setup SNMPv3 on a Cisco ASA with LibreNMS for Secure Monitoring!
My goal with this article is to monitor devices over the WAN without ports being opened.
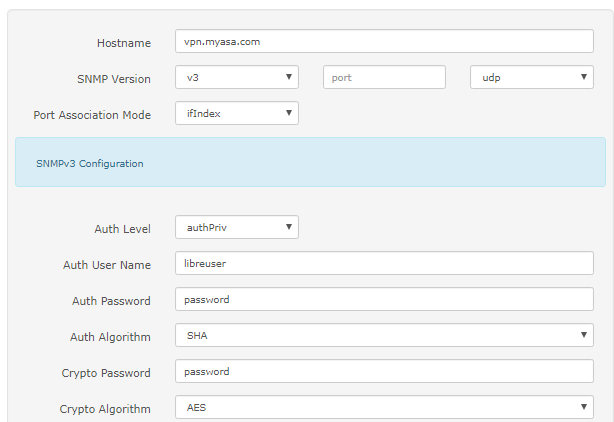
ASA CONFIG:
configure terminal snmp-server group libre v3 priv snmp-server user libreuser libre v3 auth sha password priv aes 128 password snmp-server host OUTSIDE1 1.1.1.1 poll version 3 libreuser
Notes for above: 1.1.1.1 is the WAN IP that libre is comming from, no destination NAT required, you just need the IP.
Feel free to edit the group name, the username, and the password.
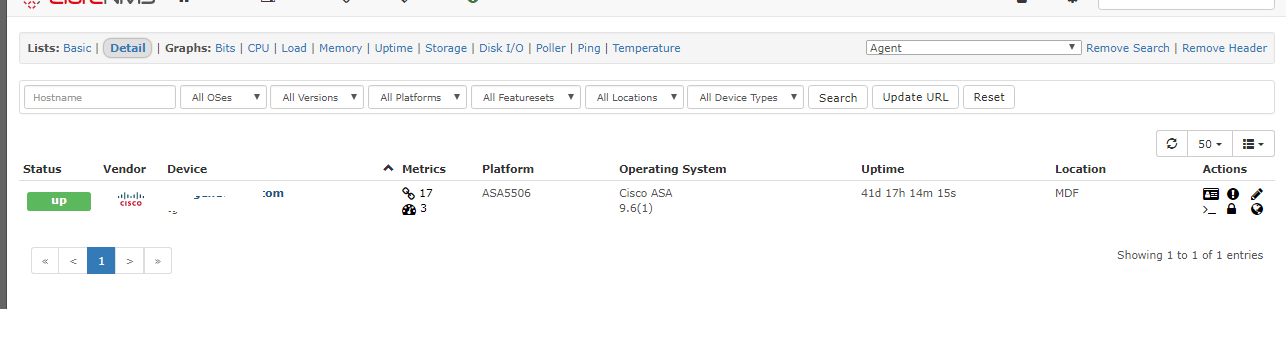
Now here is a screenshot from LibreNMS
Boom success!
One might ask, yea but is it really encrypted? Well let’s check a capture from the LibreNMS server
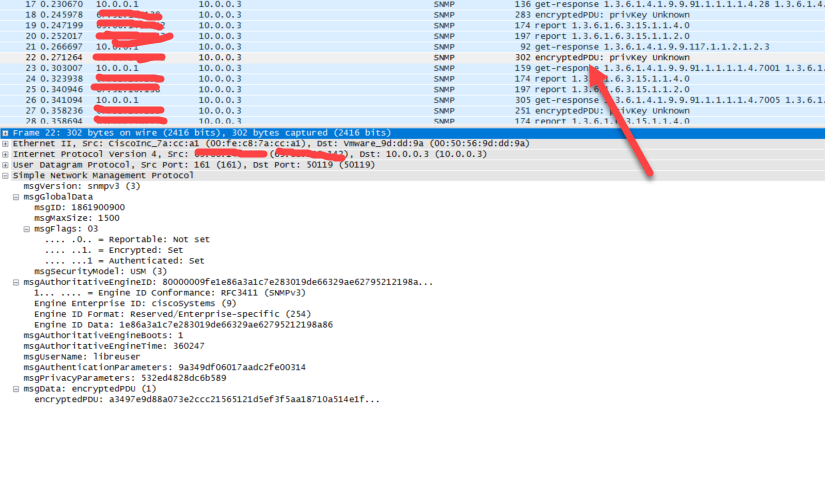
The authentication hashing we used was SHA, however it does not stop there. We are encrypting our communication with DES. So not only is the password sent as a hash, but this is all encrypted with DES while it’s happening.
What are the risks? Having a basic understanding of how network devices communicate is required to understand the low risks in this method. This being a unicast flow of packets it would only really be succeptible to man in the middle attacks. One would need to capture the packets, and then try some sort of brute forcing on that. Not only that, but it is expected and encouraged to have some sort of control plane policing. In the ASA’s case it’s built into the command. We specified which public IPs are allowed to poll us over the Outside interface. Last but not least unless you have a specific need, do not enable SNMP write. The Cisco ASA does not even support SNMPv3 write, so we did not have to declare read-only.
Overall SNMPv3 over the WAN monitoring is straight forward, secure, and highly scalable on the Cisco ASA series Firewalls!
If you’re interested in integrating oxidized with LibreNMS click here!