What problem are we trying to solve? We want to prevent the rouge DHCP Server from assinging addresses out to our clients.
Normally this would be your favorite wanna-be IT employee that brings his own Linksys router in the mix to fix the network 🙂
Of course it can also protect from malicious parties that want to hand out bad DNS servers, or bad gateways to facilitate a man in the middle attack.
When you enable DHCP snooping on a Cisco switch all ports become “untrusted” sort of like how when you enable QoS all ports are untrusted and you don’t accept their markings. We need to trust the interface the DHCP server is connected to. When a DHCP discover packet comes into a port (a client looking for a DHCP server) the switch begins the snooping process and monitors it.
The switch will learn the MAC on the port the broadcast was received then he forwards this broadcast out to all ports. DHCP snooping will prevent the client from receiving a response from a NON-TRUSTED port. The rouge DHCP server will still send the replies to the switch, however they will never make it to the client. The switch knows this because it compares the trusted DHCP server’s MAC (from the binding database dynamically) to the MAC of the rouge DHCP server replying.
DHCP snooping can also prevent floods of DHCPRELEASE and or DHCPDECLINE messages (DoS). However, by default, it doesn’t protect against DHCP DoSing the IP addresses. Rate limiting can help with that but will eventually fail. The DHCP snooping database does not survive reboots by default. You will need to configure the database agent for that that’s above the level of this post). The DHCP binding database can be used for other features such as dynamic ARP inspection and IP Source guard (topics for later posts)
The Lab:
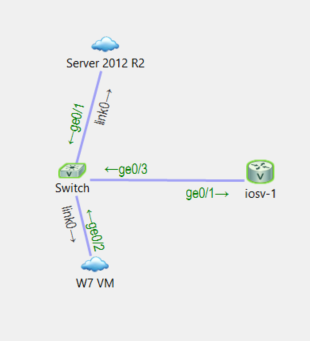
IOSV-1 is the rouge DHCP server/router.
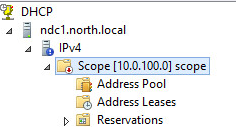
I’ve configured a server 2012R2 VM as a DHCP Server and authorized it within the domain, I’ve configured a scope on the server but disabled it, the scope is:
subnet: 10.0.100.0/24
gw: 10.0.100.1
![]()
Now let’s configure our Rouge DHCP Server (IOSV-1):
enable configure terminal service dhcp ip dhcp pool NETB network 10.0.100.0 /24 default-router 10.0.100.66 domain-name BADNETWORK.LOCAL exit int g0/1 ip address 10.0.100.66 255.255.255.0 no ip redirects no shutdown exit ip route 0.0.0.0 0.0.0.0 10.0.100.1
Notice above I gave configured the DHCP scope to make the rouge router the default gateway, then route the traffic to the normal gateway.
I also configured “no ip redirects” this disables ICMP redirects from telling the clients that the next hop is on the same vlan, this guarantees my clients traffic will pass through me.
Now currently only my rouge DHCP server is on just to illustrate a point. Notice here my W7 VM got a DHCP lease from the rouge router.
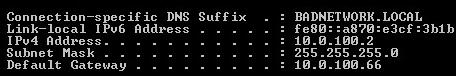
Let’s configure DHCP snooping on our switch.
enable configure terminal ip dhcp snooping ip dhcp snooping vlan 1 int g0/1 ip dhcp snooping trust
note: I’ve now enabled DHCP on my Windows Server with the below command.
![]()
remember int g0/1 is the switchport connected to the Server. Now I disable and re-enable my interface on the W7 VM. Below is the result.
Also, the “ip dhcp snooping vlan 1” is required because DHCP snooping, by default, is disabled for all vlans, even when enabled globally.
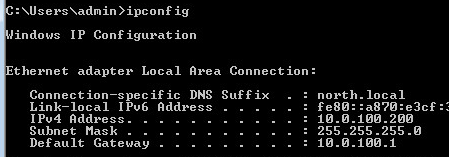
We see DHCP snooping is now working properly.
Looking for my switch debug with the command “debug ip dhcp snooping events” I get this message stating a entry was added to the database.
![]()
I can further see it’s working by checking the DHCP snooping binding database.
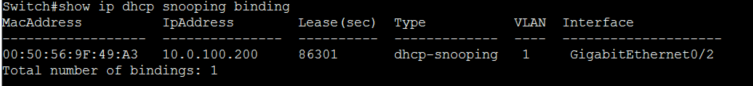
Above we see the MAC address of my Win7 VM, along with the IP it was assigned, we also see the interface it’s connected to.